Headless Browsers for Password Spraying
by Keramas
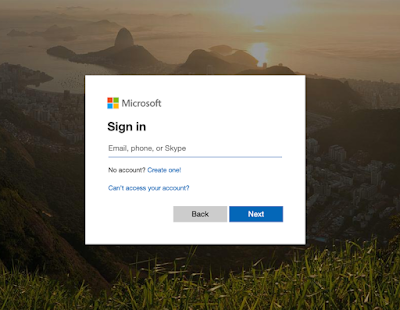
During a recent external penetration test, a client was using several Microsoft services, such as Outlook, Sharepoint, and Dynamics, wherein the logins all took place via 'login.microsoftonline.com'.After a bit of digging, a co-worker and I discovered a solution to this issue by using Python with a headless browser to make requests and search the DOM for indicators of success/failure.
The following resource set us down the proper path:
https://realpython.com/modern-web-automation-with-python-and-selenium/
If you are familiar with how to use Beautiful Soup, then you shouldn't have any issues getting started, and the above guide provides all the information you need to have your script navigate the DOM.
Using this concept and library, you can build out a password spray tool for each situation you find yourself in, it just takes a bit of manual probing to get the DOM elements correct and inserting the proper logic based on the page's functionality.
To make password spraying possible and automated in these situations, my co-worker and I developed the following tool 'domspray' so we hope that it aids in any external penetration tests or red team engagements:
https://github.com/km-zdh/domspray
As a parting note, if you are creating a script and running tests, be sure to properly close out the headless browser each time the script terminates or you are going to have a bad time! I can neither confirm nor deny why I know this...
tags: