2018 Metasploit Community CTF
by Keramas
The Metasploit Community CTF is a ton of fun and it is a bit different than your standard jeopardy CTF. Full details on the CTF can be found on the homepage, but to give a short breakdown of how it works:1. You are assigned two target boxes
2. Penetrate the targets and uncover specific playing card PNG images and md5sum them for the flag.
I was a member of team "rememberingAaronSwartz", and we managed to take second place through a ton of collaboration and hard work. In traditional CTF fashion, we put together a write up of each of the challenges to share with others and also illustrate how fun this was!
Nmap scans output from machines:
Ubuntu (172.16.4.213):
PORT STATE SERVICE
Nmap scan report for 172.16.4.213
Host is up, received conn-refused (0.0087s latency).
Scanned at 2018-12-01 02:55:28 UTC for 3555s
Not shown: 65525 closed ports
Reason: 65525 conn-refused
PORT STATE SERVICE REASON VERSION
25/tcp open smtp syn-ack Sendmail 5.51/5.17
|_smtp-commands: SMTP: EHLO 500 Command unrecognized\x0D
79/tcp open finger syn-ack SGI IRIX or NeXTSTEP fingerd
|_finger: No one logged on\x0D
2222/tcp open ssh syn-ack (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-libssh_0.8.3
---------------------------------SNIP---------------------
8080/tcp open http syn-ack Apache Tomcat/Coyote JSP engine 1.1
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
| http-title: Struts2 Showcase
|_Requested resource was showcase.action
8181/tcp open http syn-ack WEBrick httpd 1.3.1 (Ruby 2.3.0 (2015-12-25))
|_http-favicon: Unknown favicon MD5: EE9029912A80EA3845D439EF7E08ABF6
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-server-header: WEBrick/1.3.1 (Ruby/2.3.0/2015-12-25)
|_http-title: 8 of Diamonds
8443/tcp open ssl/http syn-ack Thin httpd
|_http-favicon: Unknown favicon MD5: 7E91B08265C69619AE445051AC00F125
|_http-server-header: thin
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
| ssl-cert: Subject: commonName=93f1rywa.jpnykqxgnz.az.hakqi3.gzg9xrkmq.edu/organizationName=Joan/stateOrProvinceName=RI/countryName=US/localityName=Shirley
-----------------------------SNIP-----------------------
| 5sft8b6u6TJT5w==
|_-----END CERTIFICATE-----
|_ssl-date: TLS randomness does not represent time
8777/tcp open http syn-ack nginx 1.15.6
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.15.6
|_http-title: Site doesn't have a title (text/html).
8880/tcp open http syn-ack Apache httpd 2.4.7 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Secure File Storage
9021/tcp open http syn-ack nginx 1.15.6
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.15.6
31063/tcp open http syn-ack nginx
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx
|_http-title: 3 of Clubs
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port2222-TCP:V=7.70%I=7%D=12/1%Time=5C01F829%P=x86_64-pc-linux-gnu%r(NU
SF:LL,16,"SSH-2\.0-libssh_0\.8\.3\r\n");
Service Info: Host: 2-of-diamonds; OS: Unix
Windows (172.16.4.214):
ec2-user@kali:~$ nmap -sC -sV -p- 172.16.4.214
Starting Nmap 7.70 ( https://nmap.org ) at 2018-11-30 17:25 UTC
Nmap scan report for 172.16.4.214
Host is up (0.00047s latency).
Not shown: 65520 closed ports
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
3389/tcp open ms-wbt-server Microsoft Terminal Service
| ssl-cert: Subject: commonName=WIN-F0RRKTD2VFF
| Not valid before: 2018-11-27T18:26:29
|_Not valid after: 2019-05-29T18:26:29
4444/tcp open ms-pe-exe Microsoft PE executable file
| fingerprint-strings:
| GetRequest:
| !This program cannot be run in DOS mode.
| DRich
| .text
| `.rdata
| @.data
|_ .idata
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=packer
| Subject Alternative Name: DNS:packer
| Not valid before: 2018-11-28T19:12:13
|_Not valid after: 2019-11-28T19:32:13
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49160/tcp open msrpc Microsoft Windows RPC
49161/tcp open msrpc Microsoft Windows RPC
49166/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port4444-TCP:V=7.70%I=7%D=11/30%Time=5C0172C4%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,43E0,"MZ\x90\0\x03\0\0\0\x04\0\0\0\xff\xff\0\0\xb8\0\0\0\0\0\
SF:0\0@\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\
SF:0\0\xd8\0\0\0\x0e\x1f\xba\x0e\0\xb4\t\xcd!\xb8\x01L\xcd!This\x20program
SF:\x20cannot\x20be\x20run\x20in\x20DOS\x20mode\.\r\r\n\$\0\0\0\0\0\0\0\x9
SF:cm\x99\x17\xd8\x0c\xf7D\xd8\x0c\xf7D\xd8\x0c\xf7D\xd5\^\x16D\xc6\x0c\xf
SF:7D\xd5\^\(D\xc8\x0c\xf7D\xd5\^\x17D\xb1\x0c\xf7D\x05\xf3, NetBIOS MAC: 0a:1f:9f:b2:4e:42 (unknown)
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2018-11-30 17:27:23
|_ start_date: 2018-11-30 17:14:40
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 142.00 seconds
2 of Diamonds
Host: 172.16.4.213
Port: 25
PORT STATE SERVICE VERSION
25/tcp open smtp Sendmail 5.51/5.17
|_smtp-commands: SMTP: EHLO 500 Command unrecognized\x0D
Service Info: Host: 2-of-diamonds; OS: Unix
Looking at the Nmap scan, it was showing Sendmail 5.51/5.17. Based on this, we found that this was a vulnerability utilized by the famous Morris Worm, and using the Metasploit module, we were able to access the machine as the "daemon" user.
This host was a 4.3BSD machine straight from 1986, which made it a bit difficult to move around and enumerate. Dumping the contents of /etc/passwd, there were a lot of users and hashes. These were extracted and most were cracked with hashcat + the rockyou wordlist.
The user 'hunter'; however, was not cracked initially. Exploring the box we found that there were a lot of references to the Cuckoo's Egg book and started drawing on ideas from this. Using a modified word list we were able to then crack the 'hunter' user's password: msfhack.
Logging in with that user, we found that there was a SUID movemail binary in his folder. This allowed us to move any kind of file from one place to another as root. Experimenting with this, it was seen that it also changes the permissions of the resulting file.
Looking around the box some more and correlating interesting things seen from the /etc/passwd file, we noticed that in the games directory, there was a very new file compared to the rest.
Exploring more in this directory, the lib folder contained the interesting 2_of_diamonds.dat. However, we could not do much with it due to permissions. However, using movemail allowed us to move this into the hunter folder and it changed the permissions in the process allowing us to read the file. This turned out to be an encrypted file which needed a password.
Going back to adventure, it turned out that this was a modified version of the game that you had to play to advanced in the 2 of Diamonds challenge. Playing the game with a guide, there is a flag which if you later drop along with the rest of your loot will give you the password to the .dat file: wyvern.
Unfortunately, the box was lacking most of the common means to transfer this .dat file over, so the 'od' command was used to copy and paste the data to the attack machine. We then used the 'crypt' command to decrypt the 2_of_diamonds.png.
3 of Diamonds
Host: 172.16.4.213
Port: 8777
PORT STATE SERVICE VERSION
8777/tcp open http nginx 1.15.6
|_http-server-header: nginx/1.15.6
|_http-title: Site doesn't have a title (text/html).
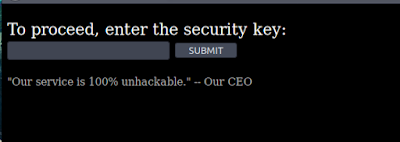
Checking out port 8777 via a browser, we are greeted with a secure file storage service.
There was a section to download file, but we needed to provide a valid key.
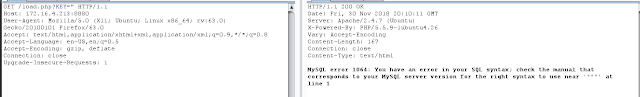
Using Burp Suite, the request sending a fake key was captured, and it was determined that this was susceptible to SQL injection through manual testing.
Saving this request to a file, sqlmap was then used to dump the database, which contained the ace_of_hearts.key (which will be used for a different challenge) and the base64 of the 3 of Diamonds.png:
The rest of the challenge writeups (including the above) can be found on my teammate MinatoTW's Secjuice blog:
https://www.secjuice.com/metasploit-ctf/
Looking forward to next year!
tags:
Windows Foothold
Host: 172.16.4.214
Port: 4444
Probing port 4444 of the windows machine with netcat resulted in a bunch of binary being dumped out. Curling this and saving it into a file, it was possible to boot this up in a Windows VM and attach it to Immunity debugger and then fuzz the running service over port 4444, which resulted in a buffer overflow.
EIP was overwritten with an offset of 1017 bytes.
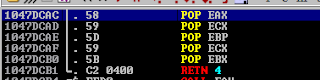
Looking at the stack after the crash, if we could find an instruction set with 5 pops + a ret, we could land right to the start of the buffer.
We managed to find just what we needed at 0x1047DCAC.
After confirming this worked, we added reverse shell shellcode to the start of our buffer and got a foothold on the box. We then set up an admin account so we could RDP into the box, and there was a treasure trove of challenges waiting to be solved.
Ace of Diamonds
Host: 172.16.4.214
Searching the Windows box beyond what was present in the administrator's desktop folder, we came across a strange executable, 'flag_finder_9000.exe" and an obfuscated PNG image.
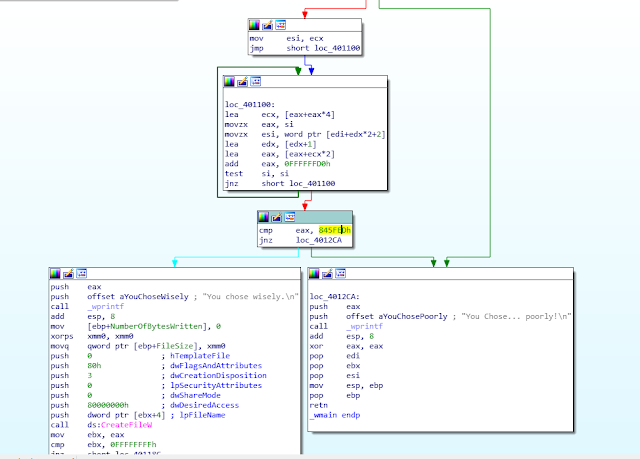
Copying both over to a VM, running the executable prompted for two arguments: filename and a magic number.
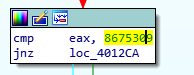
Loading the executable up in IDA, it was easy to find the check that was occurring:
Letting IDA do the heavy lifting, it revealed the magic number to be Jenny's number...
Running the executable again feeding it the obfuscated PNG file as the filename and the uncovered magic number, it spits out the Ace of Diamonds flag.
The rest of the challenge writeups (including the above) can be found on my teammate MinatoTW's Secjuice blog:
https://www.secjuice.com/metasploit-ctf/
Looking forward to next year!