Recon Village CTF @ Defcon 26
by Keramas
Defcon 25's Recon Village CTF was a ton of fun and my team was very much looking forward to participating during Defcon 26. I think in comparison to last year, this year's CTF proved to be a bit more challenging, and we decided to go full force to get top 3. It was a close race, but we were passed at the end and got knocked into 5th.Below are the challenges that were released and a write-up of the solutions. We'll be ready for another round at Defcon 27!
Challenge 1
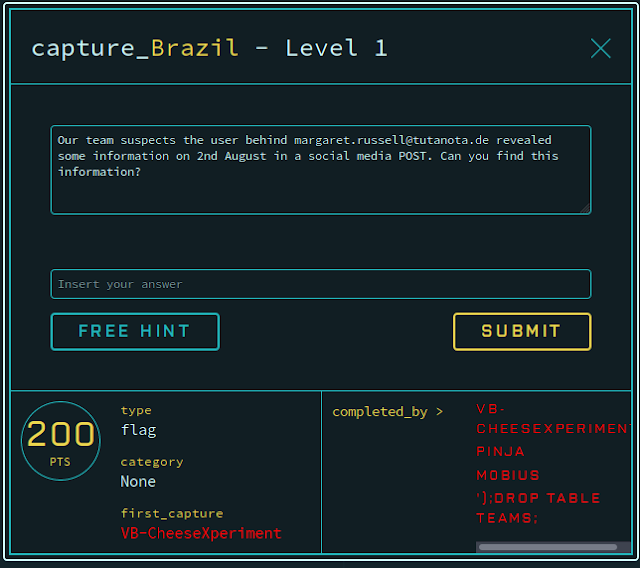
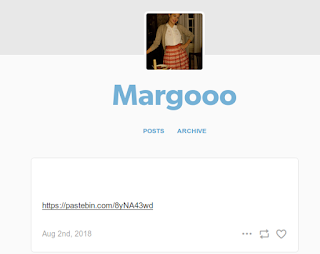
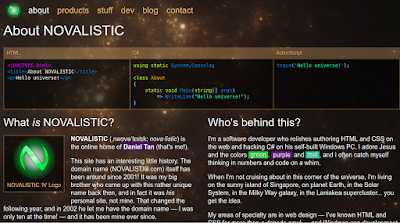
Performing a search for the email address, it was easy to determine that it was associated with a Tumblr account.
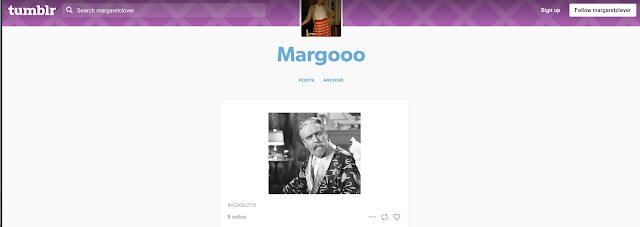
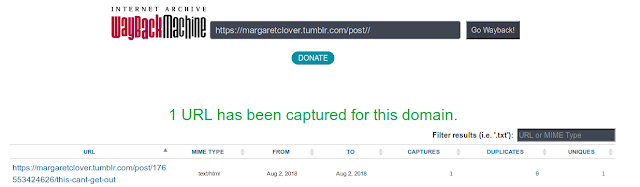
Once at the Tumblr page; however, there was no post made on August 2. Time to blast back into the past with the internet archive, the Wayback Machine.
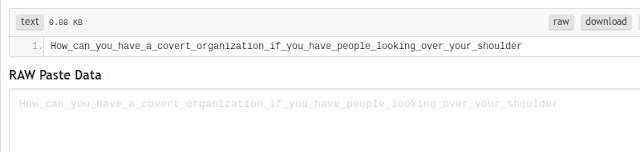
Searching for the Tumblr URL along with 'post', we find a post made on August 2 that was deleted. Following this link we arrive at the missing post:
And finally, heading to the Pastebin link, we arrive at the flag:
Challenge 2
It's easy to miss, but it's possible to scroll down in this challenge for a slight hint:
Challenge 3
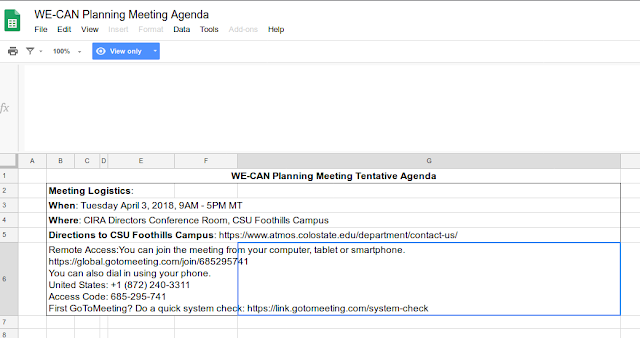
Performing a simple search on Google with the information given, it is easy to find an unprotected Google spreadsheet that contains all the meeting information as well as the GoToMeeting access code, which is the flag.
Challenge 4
Heading to the provided site, we encounter a simple web app.
Inputting a name will just return a hello, but the interesting thing to check out is the GitHub fork banner in the upper-right corner.
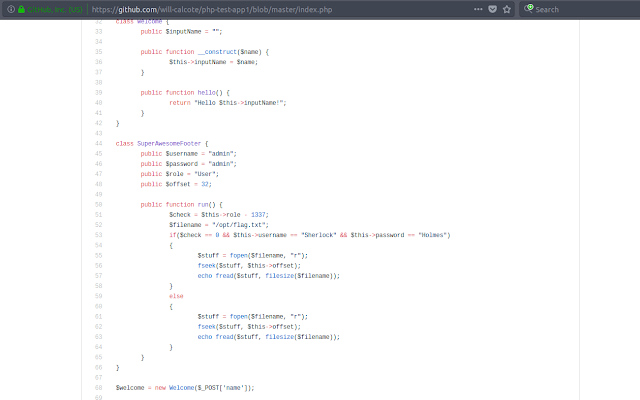
This GitHub contains the index.php resource which gives more insight into what is running on this page.
Different than the source code viewable from the browser, this shows a /opt/flag.txt will be called when certain requirements are fulfilled.
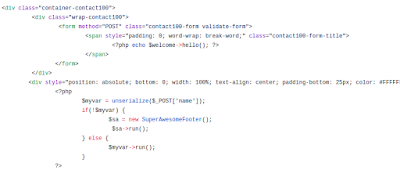
Furthermore, looking at the code some more, we see that serialization/unserialization is taking place.
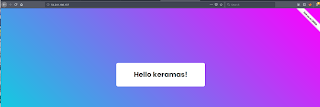
Based on this, we can serialize all of the data needed, and passing it into the input field we are able to grab the flag.
Challenge 5
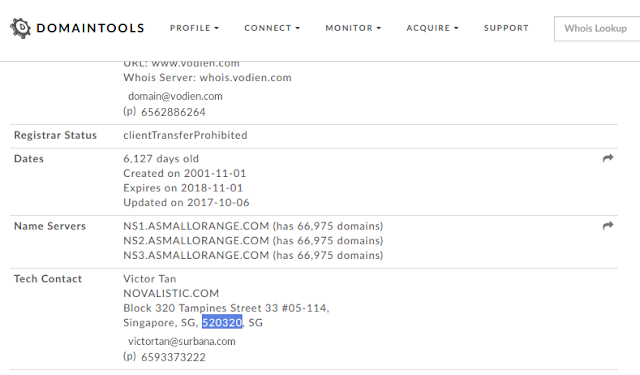
Once again using the information on hand, we head to Stack Overflow and looked up the people who earned this badge. We found the following user:
Heading to site that was listed gives a bit more information.
Finally, using a whois lookup for the domain, we find the postal code for the user, which is our flag.
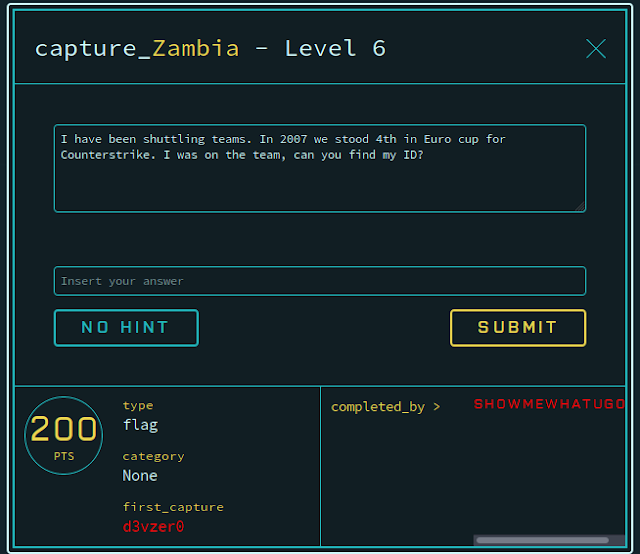
Challenge 6
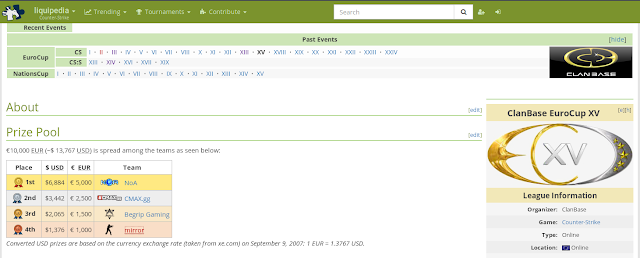
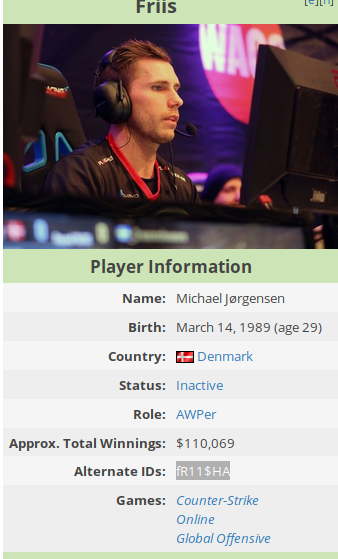
Since this is E-sports related, the best bet for information in Liquipedia. We can then zero in on the exact competition.
Our fourth place team doesn't have a dedicated page, but you can still view the roster by hovering over the thumbnail of the team logo.
Only two of the players have a page and more history playing, so it's just a matter of checking each of them out. The flag ended up being the alternate ID of Friis.
Challenge 8
The link provided is for Telegram, and upon joining the chat room, there is a bot that allows you to issue shell commands, but in a very limited capacity. However, it was possible to issue the 'ssh' command. Hoping that no password was required, we issued 'ssh' with the '-t' flag to execute a command, and we received the flag.
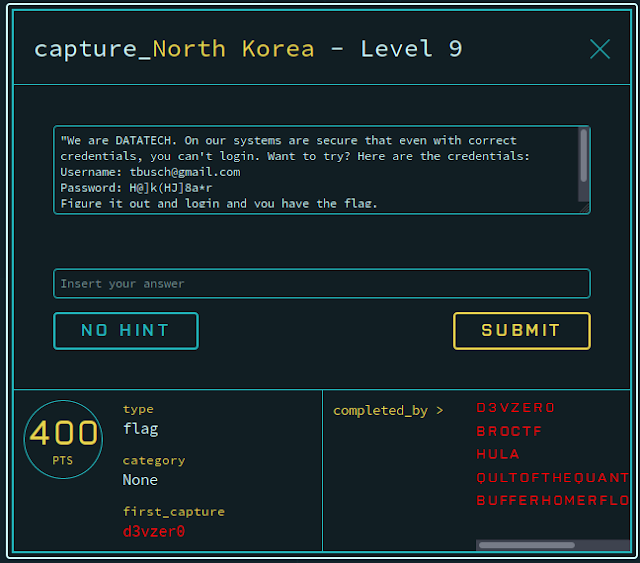
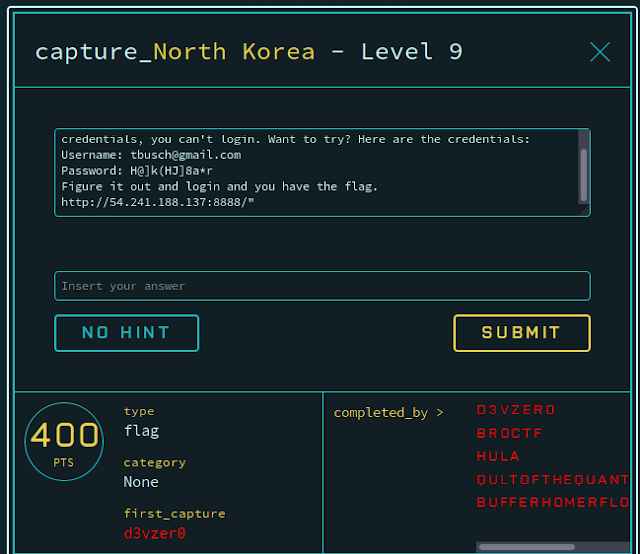
Challenge 9
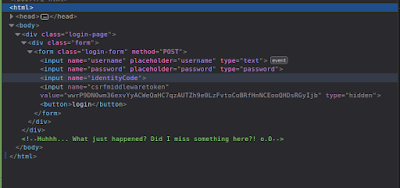
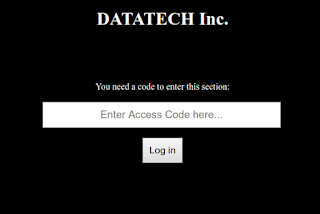
Connecting to the site, we arrive at a simple login page. As the challenge text mentioned, just using the provided creds alone will not allow us to enter the site.
Looking at the page elements, you can see a hidden input field for 'identitycode'. (I deleted the hidden parameter before the screenshot). So this is what we need to log into the site.
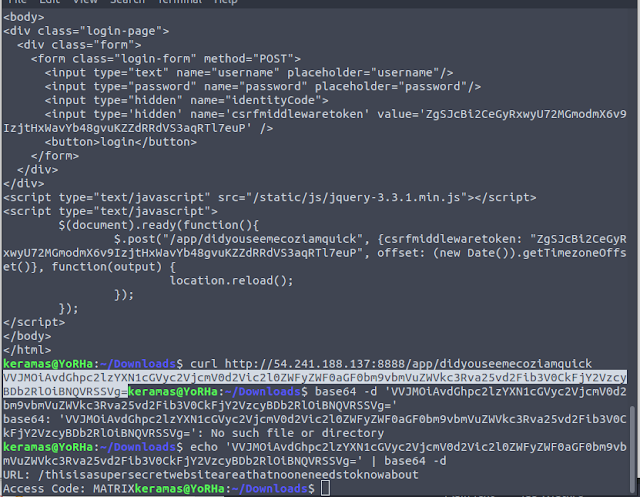
Using curl to grab all the source code, we discovered a hidden snippet of code which reveals a hidden directory. Once again using curl on this directory, we find a base64 encoded string, which reveals yet another hidden directory along with an access code.
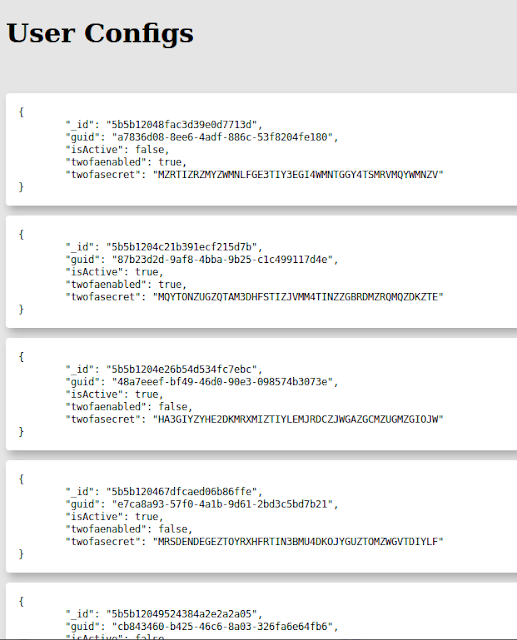
Heading to the newly discovered page, we input the access code and are gifted with a bunch of JSON data for user configs.
This is where my team got stuck, but it seems that it is possible to enter this information paired with the initial credentials in order to get a token code from Google, which can then be used to enter the site and grab the flag.
Challenge 13
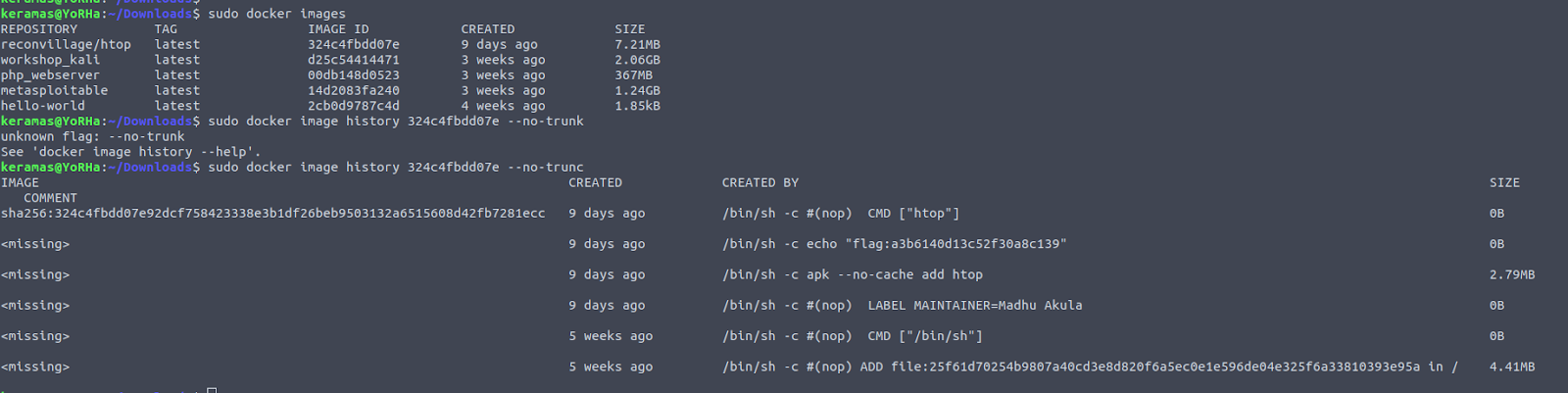
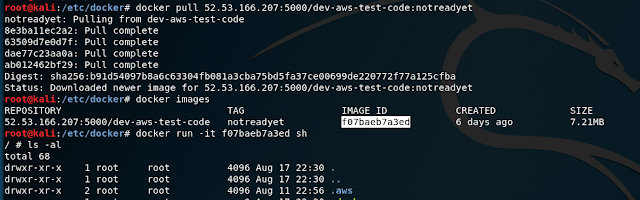
Since we know this is for a docker repository, we tried curl with the default port to get the catalog information for what repositories are available. Following up once we saw the repository, we queried this repository for the tags list.
We then did a docker pull for this image, and ran it to get a command prompt. Knowing that this has to do with AWS test code, the .aws folder looks like a great place to start the investigation.
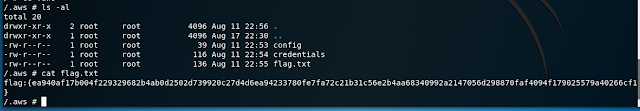
Checking out the contents of .aws, we find the flag.
Checking out the contents of .aws, we find the flag.
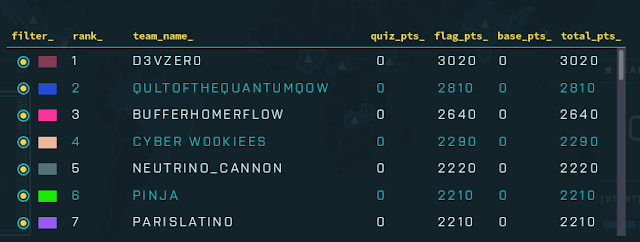
Final Tally
We had a blast participating and it w as a close race at the end to solidify the scores. Congrats to all of the winners, and a big thank you to the organizers. See you all next year!