TAMUCTF: Enum
by Keramas
This was by far my favorite challenge of the CTF since it resembled a mini boot-to-root challenge (minus actually getting root part...), which focused a lot (surprise, surprise) on enumeration.When we initially SSH in, we are dropped into a restricted shell, so first things first to make it easier on ourselves, call /bin/bash with echo 'os.system("/bin/bash")' .
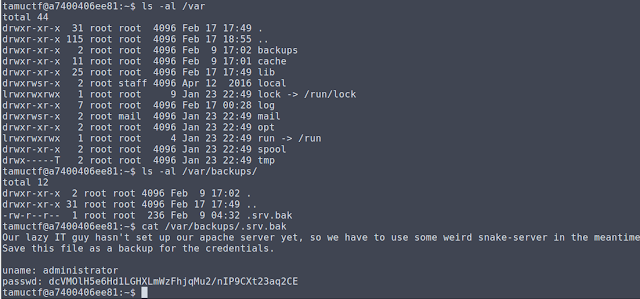
It took quite a lot of prodding around to find anything interesting, but I eventually discovered the following:
Alright, so we know they are running a pyserver of some sort. Time to find out what's going on.
Cool, it is running as root over port 9000. Now it's just a matter of finding a way to interact with it. We can do this by port forwarding to our local host with the following command:
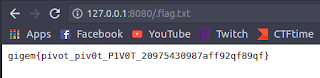
Now that it is set, all we need to do is pull up our browser and navigate to our local host and the 8080 port we indicated.
Doing so, we get the flag! tags: CTF challenge