TAMUCTF: Bandaid
by Keramas
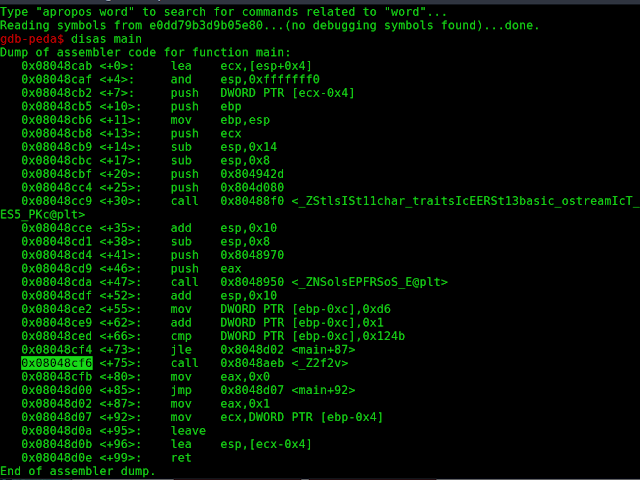
We are given a broken binary that claims it needs some fixin'!We can go about this two ways: Patch the assembly so it executes as it should OR we can just force it to execute properly in GDB by setting the EIP to the function it is supposed to execute. I went with the latter method.
Setting the EIP to the address for _Z2f2v, we continue the program and it spits out a ton of stuff.
The top portion is definitely some sort of encryption, and the two big chunks below it are a ton of base64. Wonder that that could be...
Ah--neat! So we get a private and public RSA key, which means the private key should be able to decrypt the message at the top.
Modifying an existing RSA decryption python script, we can easily decrypt our message and get our flag!
tags: CTF challenge