Shellter SHX#17 CTF
by Keramas
CTF Name:Shellter SHX#17
Category
Forensics
This was a series of three different forensic challenges.
Challenge #1: Recover

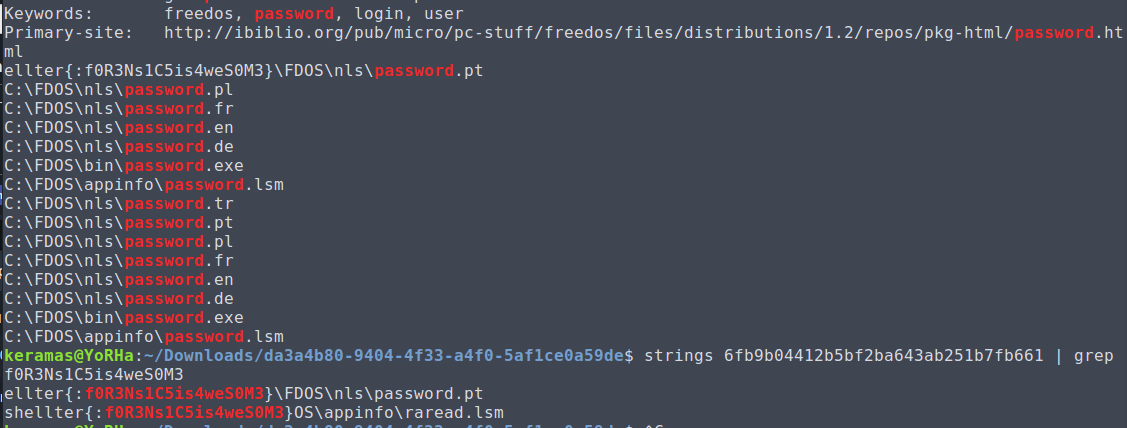
Downloading the challenge file, we can just use strings on it and grep for 'password'.
This reveals most of the flag, but using grep again for the content inside the brackets uncovers the entire flag.
Challenge #2: os.environ.get

I actually tried to mount and explore this drive image, but it wasn't leading anywhere, so back to strings!
I ran strings on the whole drive and exported it into a .txt file, and then started to search for various keywords.
Since we know the issue is with os.environ.get, we can assume it has to do with a problem with something related to "PATH=".
Searching for this as a keyword, we can find a string of hex characters with a tiny hint that says "HEX2ASCII".

So, converting from hex to ascii we get our flag!

Challenge #3: Suspicious Behavior
This challenge uses the same drive image as the prior challenge, and I haphazardly came upon this while searching for some keywords. Using "OS=" as a keyword, I found a suspicious string of what looked to me like hexidecimal characters, and sure enough, when converting them into ascii, we got our flag locating the malware!

